[Unix-Linux] SSH Commands
Categories: Unix-Linux
📋 This is my note-taking from what I learned in the Unix/Linux Tutorial!
- Reference link: https://www.ssh.com/academy/ssh/command
What is SSH(Secure Shell)?
SSH is a software package that enables secure system administration and file transfers over insecure networks. It is used in nearly every data center and in every large enterprise.
The SSH Protocol
The SSH protocol uses encryption to secure the connection between a client and a server. All user authentication, commands, output, and file transfers are encrypted to protect against attacks in the network.
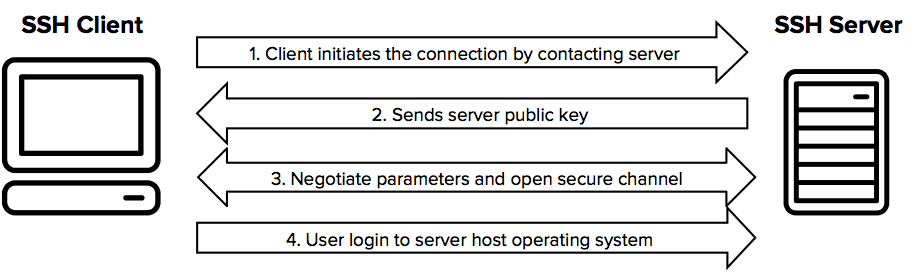
SSH Command in Linux
The ssh command provides a secure encrypted connection between two hosts over an insecure network. This connection can also be used for terminal access, file transfers, and for tunneling other applications. Graphical X11 applications can also be run securely over SSH from a remote location.
Other SSH Commands
There are other SSH commands besides the client ssh. Each has its own page.
- ssh-keygen - creates a key pair for public key authentication
- ssh-copy-id - configures a public key as authorized on a server
- ssh-agent - agent to hold private key for single sign-on
- ssh-add - tool to add a key to the agent
- scp - file transfer client with RCP-like command interface
- sftp - file transfer client with FTP-like command interface
- sshd - OpenSSH server
Working with Linux Client
Working with Linux Client
1. Using the Linux client
Linux typically uses the OpenSSH client. The ssh command to log into a remote machine is very simple. To log in to a remote computer called sample.ssh.com, type the following command at a shell prompt:
ssh sample.ssh.com
If this is the first time you use ssh to connect to this remote machine, you will see a message like:
The authenticity of host 'sample.ssh.com' cannot be established.
DSA key fingerprint is 04:48:30:31:b0:f3:5a:9b:01:9d:b3:a7:38:e2:b1:0c.
Are you sure you want to continue connecting (yes/no)?
Type yes to continue. This will add the server to your list of known hosts (~/.ssh/known_hosts) as seen in the following message:
Warning: Permanently added 'sample.ssh.com' (DSA) to the list of known hosts.
Each server has a host key, and the above question related to verifying and saving the host key, so that next time you connect to the server, it can verify that it actually is the same server.
Once the server connection has been established, the user is authenticated. Typically, it asks for a password. For some servers, you may be required to type in a one-time password generated by a special hardware token.
Once authentication has been accepted, you will be at the shell prompt for the remote machine.
2. Specifying a different user name
It is also possible to use a different username at the remote machine by entering the command as:
ssh alternative-username@sample.ssh.com
The above can also be expressed with the syntax:
ssh -l alternative-username sample.ssh.com
3. Executing remote commands on the server
The ssh command is often also used to remotely execute commands on the remote machine without logging in to a shell prompt. The syntax for this is:
ssh hostname command
For example, to execute the command:
ls /tmp/doc
on host sample.ssh.com, type the following command at a shell prompt:
ssh sample.ssh.com ls /tmp/doc
After authenticating to the remote server, the contents of the remote directory will be displayed, and you will return to your local shell prompt. -x Disables X11 forwarding.
4. SSH client configuration file
The ssh command reads its configuration from the SSH client configuration file ~/.ssh/config. For more information, see the page on SSH client configuration file.
5. Configuring public key authentication
To configure password-less public key authentication, you may want to create an SSH key and set up an authorized_keys file.
6. Configuring port forwarding
Command-line options can be used to set up port forwarding. Local fowarding means that a local port (at the client computer) is tunneled to an IP address and port from the server. Remote forwarding means that a remote port (at the server computer) is forwarded to a given IP address and port from the client machine. See the page on configuring port forwarding on how to configure them.
OpenSSH also supports forwarding Unix domain sockets and IP packets from a tunnel device to establish a VPN (Virtual Private Network).
7. SSH command line options
Some of the most important command-line options for the OpenSSH client are:
-1Use protocol version 1 only.-2Use protocol version 2 only.-4Use IPv4 addresses only.-6Use IPv6 addresses only.-AEnable forwarding of the authentication agent connection.-aDisable forwarding of the authentication agent connection.-CUse data compression-c cipher_specSelects the cipher specification for encrypting the session.-D [bind_address:]portDynamic application-level port forwarding. This allocates a socket to listen to port on the local side. When a connection is made to this port, the connection is forwarded over the secure channel, and the application protocol is then used to determine where to connect to from the remote machine.-E log_fileAppend debug logs to log_file instead of standard error.-F configfileSpecifies a per-user configuration file. The default for the per-user configuration file is~/.ssh/config.-gAllows remote hosts to connect to local forwarded ports.-i identity_fileA file from which the identity key (private key) for public key authentication is read.-J [user@]host[:port]Connect to the target host by first making a ssh connection to the pjump host[(/iam/jump-host)and then establishing a TCP forwarding to the ultimate destination from there.-l login_nameSpecifies the user to log in as on the remote machine.-p portPort to connect to on the remote host.-qQuiet mode.-VDisplay the version number.-vVerbose mode.-XEnables X11 forwarding.

Leave a comment